A fairly large proportion of the global population owns computers. The internet has brought different people together, cutting across boundaries of age, race, gender, profession, social and political preferences. People can now access diverse content whether for work or entertainment, from any computing device capable of connecting to the internet. They can send email, visit sites and forums where they can post their opinions. They can chat online and even see the other person’s face.
However there has been a new revolution, particularly in the past two decades, that has brought people even closer. This is the emergence of social media.
What is meant by Social Media?
The term social media is the collective of online communications channels dedicated to community-based input, interaction, content-sharing and collaboration. Websites and applications dedicated to forums, micro-blogging, social networking, social bookmarking, social curation, and wikis are among the different types of social media (Margaret Rouse https://whatis.techtarget.com/definition/social-media).
Some prominent examples of social networks are:
Facebook: Probably the most famous and popular social media network having hundreds of millions of active users any day. It allows registered users of the age of 13 and above to create profiles, upload photos and videos, send messages and keep in touch with friends, family and colleagues.
WhatsApp: It started out as a mobile social networking app and a web application version was also released a few years ago. Like Facebook, it has hundreds of millions of users. Facebook acquired WhatsApp a few years ago (TOI Tech
https://www.gadgetsnow.com/tech-news/Facebook-buys-WhatsApp-CEO-Mark-Zuckerberg-explains-why/articleshow/30714548.cms).
Twitter: It is a free micro-blogging service that allows registered members to broadcast short posts called tweets, limited in their number of characters. Twitter members can broadcast tweets and keep track of other users’ tweets by using multiple platforms and devices.
Google Plus: It was Google’s social networking project, designed to replicate the way people interact offline more closely than is the case with other social networking services. This website no longer allows new users to sign up and those with consumer accounts (ending in gmail.com) to use its services. It was shut down on April 2, 2019 (Google “Frequently asked questions about the Google+ shutdown” https://support.google.com/plus/answer/9217723?hl=en).
Wikipedia: The world’s largest content management system dedicated to recording and spreading knowledge. It is a free, open content online encyclopedia created through the collaborative effort of a community of users. Anyone registered on the site can create an article for publication; however, registration is not required to edit articles.
LinkedIn: A social network for professionals which recently snapped up an educational services provider named Lynda.com (Maya Kosoff https://www.businessinsider.in/LinkedIn-just-bought-online-learning-company-Lynda-for-1-5-billion/articleshow/46865136.cms).
Reddit: It is a social news website and forum where stories are socially curated and promoted by site members. The site is composed of hundreds of sub-communities, known as “subreddits.” Each subreddit has a specific topic such as technology, politics or music. Reddit site members, also known as, “redditors,” submit content which is then voted upon by other members. The goal is to send well-regarded stories to the top of the site’s main thread page (Margaret Rouse https://whatis.techtarget.com/definition/social-media).
Pinterest: It is a social curation website for sharing and categorizing images found online, like pinning interesting images on a board. Pinterest requires brief descriptions but the main focus of the site is visual. Clicking on an image will take you to the original source of the image. For example, clicking on a picture of a pair of shoes might redirect users to a shoe purchasing site (Margaret Rouse https://whatis.techtarget.com/definition/social-media).
Instagram: Instagram is a photo- and video-sharing social networking service owned by Facebook, Inc.
Blogs: Blogs are regularly updated websites or web pages, typically run by an individual or small group, which are written in an informal or conversational style. For example, https://idratherbewriting.com/ is a blog on technical communication. Blogs allow communication of ideas and facts in a personal way and create a brand for the person or people behind the blog.
Social media have a tremendous impact on society and the user or membership base of such sites and services run into billions. For example, hundreds of millions of photos and videos are shared daily on Facebook alone! The infrastructure that goes behind serving such a large user base with high performance services is mind-boggling. The user base is only going to grow according to future projections (Statista 2019 https://www.statista.com/statistics/278414/number-of-worldwide-social-network-users/) (See Figure 1 for user statistics).
Social media have recently been adversely impacted by government censorship, especially in countries with conservative regimes like China (Wikipedia https://en.wikipedia.org/wiki/Internet_censorship_in_China). However, the means to circumvent such obstacles to social media access do exist. They are of two kinds: (1) accessing international sites through virtual private networks (VPNs) and (2) home-grown social media services like Weibo in China.
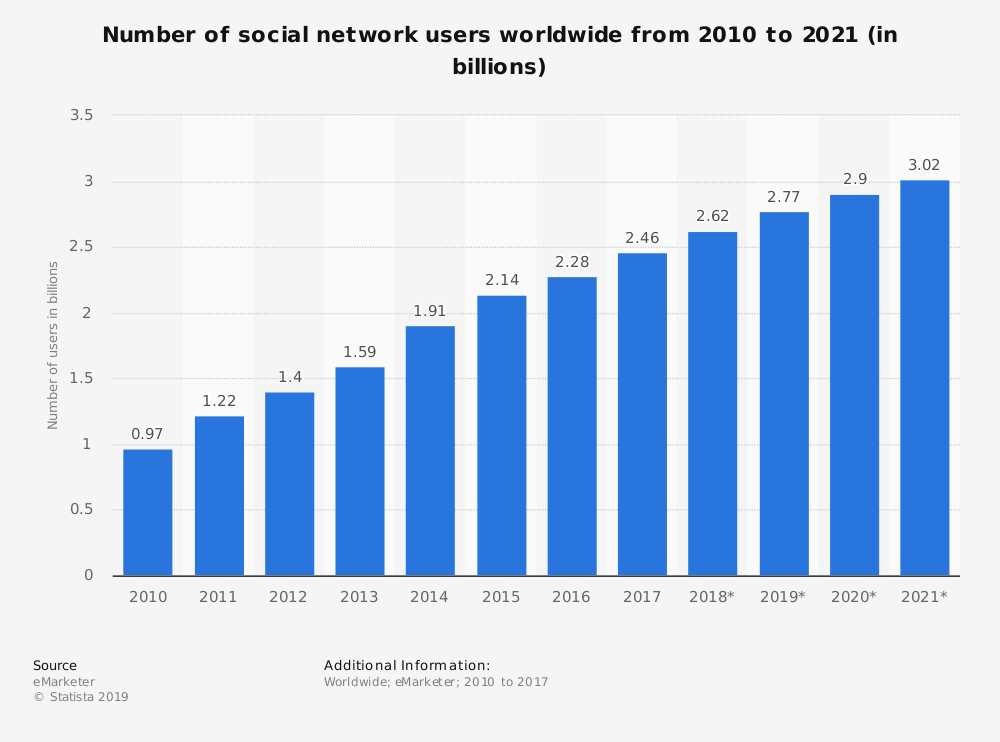
Figure 1. Number of social network users worldwide. Source: “Number of global social media users 2010-2021” https://www.statista.com/statistics/278414/number-of-worldwide-social-network-users/
How are Social Media changing Socialization and society?
Social media are changing society and socialization radically. Society is becoming more open and connected. Users tend to share even the most intimate details of their daily life with the online community, bordering on exhibitionism. There is a tendency to befriend someone whom you don’t know all that well. It is as easy as a mutual exchange of messages of consent. It works even if you don’t know that person in the offline world.
Social media give you the ability to create a fake persona. Other people in contact with you will base their opinions and emotional responses on this fake persona. On the other hand, if you give genuine information about yourself, it is easier to spy on you.
You can keep track of contacts all across the world, even when you relocate from one city or country to another. You can update your new location on your profile. You can also keep your contacts posted about the happenings in your life, wherever you are.
How do Social Media Help?
You can stay in touch with contacts whenever you are online and wherever you may be located. You can share photos and keep track of the changing look of the other person or people. One can capture precious moments on video and share them with their online friends. You can chat with contacts online whenever they are available.
You can form an online community with like-minded people. You can share your interests, hobbies and anything else with other people, reaching across geographical and social boundaries.
Social media are especially useful for staying in touch with friends, family and colleagues. You might even find your former friends, former partners and former colleagues online (See Figure 2 for benefits of social media to seniors).
In testing times like the COVID-19 pandemic, when we cannot step outside our homes and be part of a social gathering because of lockdowns, social media help us remain in touch even when we are under quarantine.
Social media lend a social aspect to entertainment like multiplayer and role-playing games. You can compete with friends or help them in difficult situations and boast of your high scores! Businesses can benefit from users playing games developed by them by introducing in-game advertising and purchases.
Social media help us keep in touch with what is trending and popular. It puts your finger on the pulse of the people. Businesses can benefit from this. They can do targeted advertising, i.e. advertising based on user preferences in things ranging from food to fashion, entertainment and even consumer electronics.
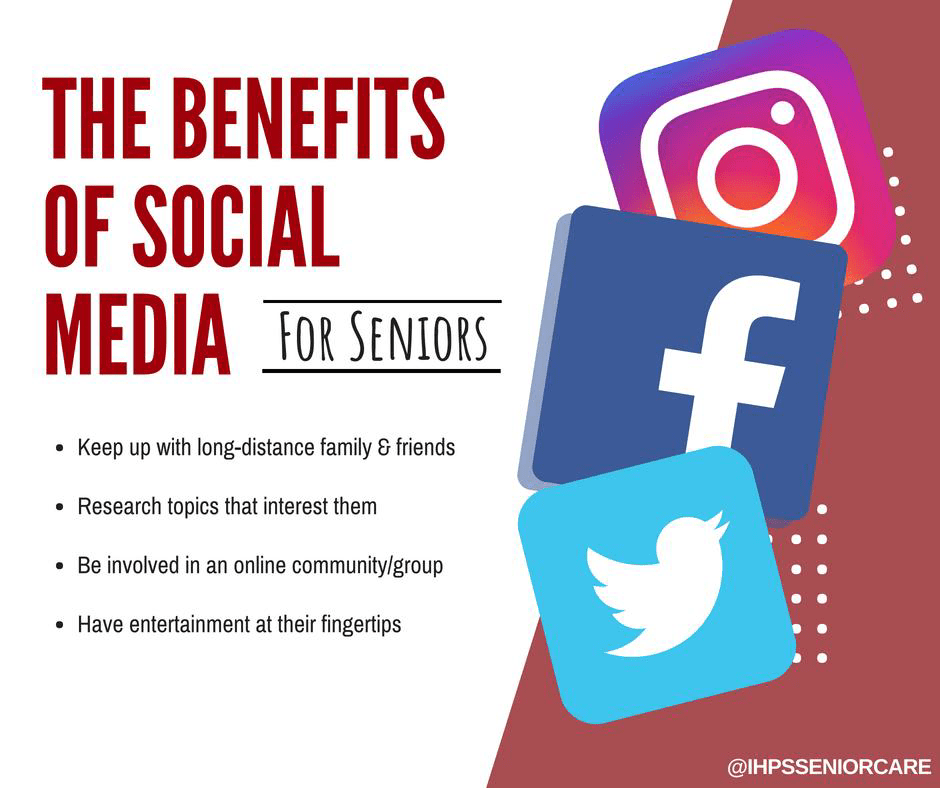
Figure 2. Benefits of social media to individuals, especially seniors.
Source: “Benefits of social media for seniors”
https://ihps.com/benefits-social-media-seniors/
Knowledge-sharing communities like Quora and Stack Overflow are of tremendous help to people from all fields. Quora is a general-purpose question and answer site. Stack Overflow is for information technology and computer programming specifically. People can post their queries regarding any topic of choice and get answers from community members.
Social media are also helping political activists in gathering more signatories for their causes and petitions. They can post a petition on a social media site/service and tell users about it. These users can then choose to indicate that they support the petition.
Social media help businesses to communicate more with prospective clients. They drive internet traffic to the business’s website, creating more awareness about their products and services. It also helps in revenue growth through more sales. (See Figure 3 for benefits for business.)

Figure 3. Businesses can benefit from social media marketing in numerous ways.
Source: “7 Side Effects of Social Media”
https://visual.ly/community/infographic/social-media/7-side-effects-social-media/
How do Social Media hurt?
Just as social media can help, they can also hurt. Criminals and malicious individuals can take advantage of their new contacts and commit crimes against them. These crimes include rape and murder, apart from cheating and fraud. The trouble starts when the would-be victims decide to meet their so-called online friends in the real world, not suspecting their mala fide intentions (Press Association https://www.theguardian.com/media/2012/dec/27/social-media-crime-facebook-twitter). (See Figure 4 for Crimes against women in India.)
Criminal gangs spread illegal content using social media including stolen goods and services. For example, they may put up stolen credit card numbers and verification numbers for visitors to misuse them.
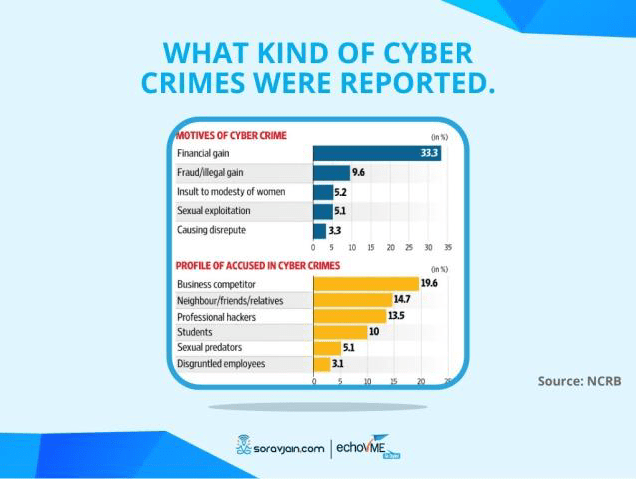
Figure 4. Crimes are committed against women in India.
Source: “7 Cyber Crimes on Social Media Against Women [India]” https://www.slideshare.net/soravjain/7-cyber-crimes-on-social-media-against-women-india/
Social media are also used for spreading misinformation or controversial and provocative content. This can lead to communal violence because of the inflammatory nature of the content. Fake news can even influence the outcome of elections, subverting a democracy’s functioning. For example, the presidential elections in USA in 2016 were rumored to be influenced by fake news about certain candidates on sites like Facebook (Danielle Kurtzleben https://www.npr.org/2018/04/11/601323233/6-facts-we-know-about-fake-news-in-the-2016-election).
No matter how secure creators of social networks try to make their social networking sites, hackers can always devise means to obtain personal information of users and misuse it. They can also target celebrities.
Opportunistic and unethical individuals can create fake profiles in the names of individuals or national ministries or governments. They can then get contact information of people who think they are chatting with the real person(s) (Matthew Herper https://www.forbes.com/2009/04/24/facebook-privacy-herper-business-media-facebook.html#6f99db037288).
Confidential personal data can be sold by unprincipled social networks for financial gains. It may be sold to advertisers. Your profile may be free to create on such sites but you are the product! (Julia Carrie Wong https://www.theguardian.com/technology/2018/mar/28/facebook-apple-tim-cook-zuckerberg-business-model)
Students lose out on valuable study time spending too much time on sites like Facebook. Employees of corporate organizations damage office productivity by accessing social media sites from office networks which have nothing to do with their work. Creating network access policies against such sites may become futile in certain cases where employees can use their own devices and internet dongle, known as BYOD which stands for “Bring Your Own Device”.
Social communication is becoming addictive because some services are designed for addiction using principles of psychology. Some sites are even known to cause the reward centers of the brain to be affected during usage (Haley Cummings http://www.collegiatetimes.com/lifestyles/the-effect-of-social-media-on-the-brain/article_f27b5a1e-b999-11e7-bfc2-77d77ccdf0b1.html).
A business’s page or posts can be down-voted deliberately by users with malicious intent. On the other hand, giving businesses control over which reviews to display will give them the power to filter out negative reviews completely.
Employers can base their hiring decisions on the candidates’ social media profiles. So, a person who likes to take a walk on the wild side may not get hired at all, despite having the necessary skill-sets! (Saige Driver https://www.businessnewsdaily.com/2377-social-media-hiring.html)
There are far-reaching psychological and biological effects of social media use. Cyber-bullying and cyber-stalking have a devastating impact on the lives of the victims. Even without the presence of a persecutor, you may feel anxious, sleepless and depressed. Night-time use of social media disrupts your sleep cycle and your body’s natural bio-rhythms. Constant bombardment of near-perfect images of celebrities and actors or models, especially on Facebook, Instagram, etc, can give you a negative body-image. You may begin to think you are too fat or thin or ugly, even if you are not! (Anya Zhukova https://www.makeuseof.com/tag/negative-effects-social-media/)

Figure 5. Social media use can cause anxiety, sleeplessness and depression.
Source: “7 Negative Effects of Social Media on People and Users” https://www.makeuseof.com/tag/negative-effects-social-media/
Conclusion
Social media bring people together but can also hurt the interests of those people. However, the interaction on social media cannot be a substitute for face-to-face meetings with a close group of friends. Social media can help you stay in touch but can also spread malicious misinformation. It can also put your private/confidential data up for grabs in dubious online communities.
Businesses can tap the consumer market by reaching out to users of social media. They can target users in their advertisements because they know their preferences. This is a potential privacy concern. Social media are like a double-edged sword and must be used cautiously.
You should strike a balance between your online as well as offline lives and apply the same prudence to your online life that you would apply to your life in the offline world.
References
1. Margaret Rouse “Social media” https://whatis.techtarget.com/definition/social-media
2. TOI Tech “Facebook buys WhatsApp: CEO Mark Zuckerberg explains why”
https://www.gadgetsnow.com/tech-news/Facebook-buys-WhatsApp-CEO-Mark-Zuckerberg-explains-why/articleshow/30714548.cms
3. Google “Frequently asked questions about the Google+ shutdown” https://support.google.com/plus/answer/9217723?hl=en
4. Maya Kosoff “LinkedIn just bought online learning company Lynda for $1.5 billion” https://www.businessinsider.in/LinkedIn-just-bought-online-learning-company-Lynda-for-1-5-billion/articleshow/46865136.cms
5. Statista 2019 “Number of social media users worldwide from 2010 to 2021 (in billions)” https://www.statista.com/statistics/278414/number-of-worldwide-social-network-users/
6. Wikipedia “Internet censorship in China” https://en.wikipedia.org/wiki/Internet_censorship_in_China
7. Press Association “Social media-related crime reports up 780% in four years” https://www.theguardian.com/media/2012/dec/27/social-media-crime-facebook-twitter
8. Danielle Kurtzleben “Did Fake News On Facebook Help Elect Trump? Here’s What We Know” https://www.npr.org/2018/04/11/601323233/6-facts-we-know-about-fake-news-in-the-2016-election
9. Matthew Herper “I Was Impersonated On Facebook” https://www.forbes.com/2009/04/24/facebook-privacy-herper-business-media-facebook.html#6f99db037288
10. Julia Carrie Wong “Apple’s Tim Cook rebukes Zuckerberg over Facebook’s business model” https://www.theguardian.com/technology/2018/mar/28/facebook-apple-tim-cook-zuckerberg-business-model
11. Haley Cummings “The effect of social media on the brain” http://www.collegiatetimes.com/lifestyles/the-effect-of-social-media-on-the-brain/article_f27b5a1e-b999-11e7-bfc2-77d77ccdf0b1.html
12. Saige Driver “Keep It Clean: Social Media Screenings Gain in Popularity” https://www.businessnewsdaily.com/2377-social-media-hiring.html
13. Anya Zhukova “7 Negative Effects of Social Media on People and Users” https://www.makeuseof.com/tag/negative-effects-social-media/